New iOS 6.1 Lock Screen Bypass Bug Found; But Does It Really Expose Your iPhone File System?
Binu Paul email: b.paul@mobilenapps.com
It appears the iOS 6.1 troubles are far from over despite Apple seeding iOS 6.1.3 beta 2 fixing the much-publicized lock screen passcode bypass bug. The passcode bypass vulnerability refuses to vanish from the Apple software with the discovery of a new lock screen bug that allows anyone to access the internal data of the iPhone by simply plugging it into a computer via USB.
The second bug of the similar nature to surface this month, the vulnerability was first posted on the Full Disclosure mailing list by Vulnerability Lab CEO Benjamin Kunz Mejri. The bug apparently allows attackers to access users' photos, contacts and more by following a series of steps on an iPhone running iOS 6.1.
The new method starts quite similarly as the one highlighted earlier this month by manipulating the phone's screenshot function, its emergency call function and its power button. The attacker can make an emergency call on the iPhone, cancel it while holding the power on and off to gain temporary access to the device. A video posted on the advisory shows a user browsing through the phone's voicemail list and contacts list while holding down the power button.
"The difference between the first exploit and this one is how it can make the iPhone screen go black, allowing an attacker to plug the device into a computer via USB and access the user's data without having their PIN or passcode credentials," Ars Technica notes.
Check out the video below that explains the bypass method:
Here is an extract from Mejri's advisory:
"The vulnerability is located in the main login module of the mobile iOS device (iPhone or iPad) when processing to use the screenshot function in combination with the emergency call and power (standby) button. The vulnerability allows the local attacker to bypass the code lock in iTunes and via USB when a black screen bug occurs. The vulnerability can be exploited by local attackers with physical device access without privileged iOS account or required user interaction. Successful exploitation of the vulnerability results in unauthorized device access and information disclosure."
However, there are conflicting reports on the potential reach of this vulnerability. Confronting the nature of the bypass bug, The Next Web says it has conducted some tests and uncovered that the bug does not allow access to your iPhone's file system. "It allows you no access to anything, not pictures, not contacts and certainly not the file system," the report said while acknowledging the existence of the vulnerability and its ability to bypass the lock, or to bring you to a blank black screen with just the status bar.
most read
more stories from What's Hot
-
Grand Theft Auto Online (GTA Online) launch issues: Rockstar details bug fix status
Rockstar Games has acknowledged the most common GTA Online launch issues and detailed the bug fix status for each problem it's currently working on.
ernest hamilton -
Target announces Brigthspot prepaid mobile service to debut on Oct. 6
Target has announced its new prepaid mobile service, Brightspot, which will debut on Sunday, Oct. 6.
ernest hamilton -
Hulu Plus now works with Google’s Chromecast streaming dongle
Hulu has added support for Google's Chromecast streaming dongle, allowing Hulu Plus users to 'cast' video directly to Chromecast.
ernest hamilton -
Grand Theft Auto (GTA) Online finally goes live
The much-awaited Grand Theft Auto (GTA) Online mode has finally gone live, unfolding a whole interconnected universe.
ernest hamilton -
BlackBerry blames $935 million hit on the BlackBerry Z10 – Q2 fiscal results are not pretty
BlackBerry has posted its Q2 fiscal results and blames a $935 million hit on 'Z10 Inventory Charge'
ernest hamilton -
Android KitKat contest reaches India with a chance to win the new Nexus 7 (2013)
The KitKat contest has now reached India, bringing promotional packages with the chance to win a new Nexus 7 (2013).
ernest hamilton -
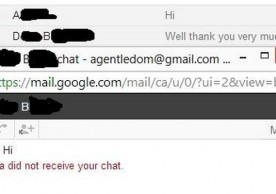
Google Talk (Gchat) messages reach wrong recipients – Careful what you say now
Google Talk has been sending messages to the wrong recipients, raising some serious privacy concerns.
ernest hamilton -
Grand Theft Auto V (GTA 5) makes whopping $800M on launch day, dethroning Call of Duty: Black Ops 2
Grand Theft Auto V publisher Take-Two has announced that the new GTA 5 made a whopping $800 million on launch day, breaking the record previously set by Call of Duty: Black Ops 2.
ernest hamilton